Authorities are not in the habit of publishing information by putting it on their websites, but by putting it printed on paper on the front door. It can easily happen that you can find out on the website when the office is open, and when you get there, you find out that it is closed. It is therefore more practical to submit and sign documents electronically. Technically, it is quite complicated, and as is usually the case, even more complicated in the state version.
What it is
An electronic signature (for people outside IT) means anything. In the case of the financial administration, it can be just a simple compression of data. You will not go to the filing office with a completed form, but with its compressed form. More precisely, with a unique identifier of the electronically completed and submitted form. The whole process of computerization actually has 4 stages, all of which run simultaneously. This is similar to the concurrent support of Windows 7, 8, 8.1 and 10 operating systems.
- Manually signing a hand-filled paper form that has been submitted physically.
- Manually signing a printed form that has been completed electronically but submitted physically.
- Manually sign a form identifier that has been filled out and submitted electronically.
- Electronic signing of an electronic form that is sent electronically together with its electronic signature.
Intuitively, you can save yourself a lot of work by skipping steps 2 and 3. However, the agile approach is modern today. It seems that only insiders know why aircraft are not serviced in flight, but always on the ground in a hangar, where the execution of the work cannot endanger any passengers.
A personal certificate can be used to sign emails or documents. A signature is trusted as much as the certification authority (CA) or all certification authorities in the chain are trusted. From signatures that will be recognized by the state, I would expect personal certificates for state purposes to be issued by the state CA. However, this is not how it is built. The state considers some already established certification authorities to be qualified (QCA). They issue qualified personal certificates. While a regular certificate creates regular electronic signatures, a qualified certificate creates qualified electronic signatures. You will not succeed with a state administration with a regular (commercial) electronic signature. (Or simply for geeks – only certificates of qualified certification authorities are installed in the government operating system.)
It is a national tradition that the Czech Republic must always have something extra. As you probably know, a certificate can have various extensions. We are interested in two:
- Client identifier of the Ministry of Labour and Social Affairs (ID card of the Ministry of Labour and Social Affairs) and
- A private key storage flag in a qualified resource (QSCD). According to information from the Czech Post , the situation is that some Czech state administration offices require the first expansion. But at the same time, the EU requires member states to recognize certificates with the second flag in their state administration.
It is probably naïve to think that absolutely every qualified certificate issued in the EU will have an ID card of the Ministry of Labour and Social Affairs, right? According to the EU regulation, the state administration may not reject any electronic signature with a certificate from QCA from any member state with QSCD expansion. National extensions, by which the ID card of the Ministry of Labour and Social Affairs are not mandatory. In practice, however, I consider it a complete waste of time to demand something like this.
Nomenclature
To make matters worse, the Financial Administration uses the term advanced electronic signature (ZAREP) for a change. It is a signature created by a regular (commercial) personal certificate, which is extended by the ID card of the Ministry of Labour and Social Affairs. (The same term is also used by the EU, but it means something completely different.) If the signature is created by an accredited (qualified) certification authority, it is a qualified electronic signature (but not from the EU point of view). In addition, if the qualified certificate is extended by the ID card of the Ministry of Labour and Social Affairs, it is a recognized electronic signature. In order for the signature to be qualified from the EU point of view, the certificate must have the private key stored in a qualified device (QSCD) flag. If it does not have one, it is (from the EU’s point of view) a (different) advanced electronic signature (based on a qualified certificate). If it does, it is a (real) Qualified Electronic Signature (QES).
What’s the problem
Many quality articles have been written on the issue related to the eObčanka. For myself, I would just say that a kind of flag that you only notice when you know to look for it makes the difference between whether you actually get a certificate with which you can create qualified electronic signatures, or only advanced electronic signatures, based on a qualified certificate. The qualified electronic signature must be stored on a device from which the private key cannot be exported. And that means you must use this device when you make a certificate request. According to EU logic, only a Qualified Signature Creation Device (QSCD) can create qualified electronic signatures. This follows from EU Regulation No. 910/2014 (eIDAS). Such a device can be (but not only) an eOP.
The whole thing looks like a marketing trick to the citizens. I think that the creation of qualified certificates should only be possible with the QSCD storage flag and also that every qualified certificate issued by a domestic certification authority should be extended by the ID card of the Ministry of Labour and Social Affairs. Otherwise, you may receive a qualified certificate that will not be valid for the Czech authorities (although it is in conflict with EU law).
What is it for?
An entrepreneurial natural person accustomed to sailing through the bureaucratic jungle like an icebreaker through an ice sheet has it easy. She doesn't find anything special. (Although it’s actually sad.) I would highly recommend a non-entrepreneurial individual to go to the office, even if it is a few kilometers away, on foot. It will be faster. An electronic signature is useful, or even mandatory for some tasks. Health insurance companies solved electronic filing themselves a long time ago, and the Czech Social Security Administration can do with an eOP (ID card with an electronic chip) even without a qualified personal certificate.
It is also possible to communicate with the authorities using data boxes. Given that the court had to order the publication of their security audit , and given that the Czech Post sends spam to these mailboxes and given that when programming the client for them, I received error messages from the internal database when using their API in the HTTP response, I would not entrust the data box with the reservation of a cinema ticket, let alone communication with the authorities. Not to mention that once you have it, you are obliged to use it for other tasks (such as tax returns) that could previously be handled on paper at a brick-and-mortar branch of the state administration. And on top of that, the mailbox cannot be canceled. On the other hand, such a certificate will simply expire one day and you will only say to the office: “Hm, bad luck. You have me here at the registry again.”
What You'll Need
Hardware
An ID card with an electronic chip, a smart card reader, a few hundred for a certificate, a printer, a few A4 sheets, a pen, an email address, a supported operating system (Windows, macOS and Linux are usually supported) and nice weather for a walk to a Czech POINT (or other qualified certification authority).
The right choice of reader is relatively important. From a technical point of view, the reader needs to meet the ISO/IEC 7816 standard, support the CCID protocol and the PC/SC communication standard. On Windows, you also want a device whose driver is Windows Hardware Quality Labs (WHQL). Last but not least, nowadays it is advisable for the driver to work in Memory integrity mode in Kernel isolation in Device security in Windows Security. It’s also a very good idea to have a device that has a hardware keyboard for entering pins. There is a security reason for this. If your operating system is infected with a keylogger, it will be of no use. The pin you enter directly into the card reader is not seen by the operating system (only the reader firmware) and therefore cannot be eavesdropped on by any application you currently have running (even if only in the background). And you don't even have to know about its installation.
I wish you good luck in finding a device that meets the intersection of all safety and technical requirements. For myself, I can recommend Gemalto IDBridge CT710 in combination with Windows 10 version 20H2 build 19042.630 (at the time of writing this article). It works for me even when memory integrity is turned on. (I only had a problem with it when I turned on the integrity. Older drivers were not compatible. All I had to do was uninstall the device and its drivers, turn on memory integrity, plug the device back in, and let Windows Update do its job.) Devices see Windows as Ezio Shield PinPad. Ezio is the name of the Gemalta product line. It was recently bought by Thales Group.
Software
The eObčanka – identification application serves as a means between the web browser and the smart card reader driver. It is written in . NET, which pleasantly surprised me. You won't find it in the Microsoft Store, so you update it like idiots and you have to periodically check the publisher’s website to see if they have released a newer version. (Classic transfer of responsibility from the service provider to the end user.) The user interface is nice. For me, 4.5 stars out of 5 (half a star for not being in the Microsoft Store).
The eObčanka – card manager application is similar from a technical point of view. It is used to control the eOP – displaying stored certificates, importing and deleting them, changing access pins, and so on. If your reader supports hardware pin input and you have the correct drivers, the pin is not entered through this application, but through the reader. As you will read below, unfortunately, this is not a matter of course. For me, one big minus is that when this application wants to enter IOK, it writes on the hardware reader that it wants to enter the PIN. After some time, you will get used to it, and when another application asks you for a real PIN, you will enter the IOK. You can easily block your ID card after three unsuccessful entries.
Application
Submitting a certificate signing request (CSR) is associated with a lot of bureaucratic sauce. In my opinion, completely unnecessary.
This section is specific to a specific CA. I chose PostSignum because I wanted to give the state (and its state-owned companies) a chance to improve their reputation with me. However, it turned out to be the exact opposite. Next time, I'd rather pay more and use the better services of I.CA or eIdentity. I would also recommend this procedure to macOS users, or to those who use their favorite Linux distribution, whatever it is.
The main thing where everything can be completely messed up is reading manuals. You must not follow PostSignum’s instructions, nor must you follow the instructions provided by iSignum itself. If you leave the Zálohovat privátní klíč box checked when generating the request and a qualified resource is selected, the application will ask you if you want to send the request even though it is not possible to back up the private key. It gives the impression that the backup of the private key is very important. But in reality, this is exactly what you certainly don't want from a security point of view. Do you want to have a QSCD from your ID card. The correct setting is as follows:
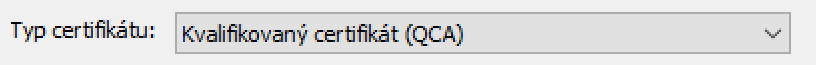
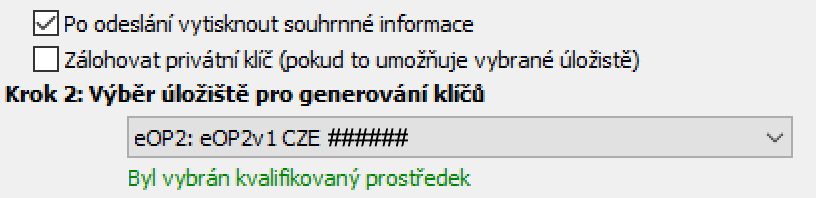
Even if you do it differently, nothing happens in reality. The Czech authorities don't need it. For them, a qualified certificate is also a certificate without the QSCD storage flag, which is what you get when the key is generated not by this device, but by your operating system. Actually, you don't have to see it as a bug, but as a feature. A certificate with geographically limited validity is something that is truly unique in the electronic world.
However, if you don't want to be seen as an idiot abroad, it’s good to have everything right. It happened to me that my biometric passport didn't work in London. Probably because it was issued before mid-2008 and the electronic chip in it did not yet contain digital fingerprints. If the Czech authorities issue you something, it does not mean that it meets the standards common in developed countries.
Don't forget to apply for the ID card of the Ministry of Labour and Social Affairs. For clarity, this is filled in elsewhere, namely on the document Údaje pro vydání certifikátů. If your ID card certificate was not available to the Ministry of Labour and Social Affairs and the private key was generated on a qualified device, the electronic signature should theoretically be valid in all EU Member States. That is, even in the Czech Republic. Theoretically. If we don't consider state implementation, let alone implementing regulations, right.


Also, don't forget to apply for a qualified certificate. Theoretically, a commercial certificate with the ID card of the Ministry of Labour and Social Affairs should be sufficient for the Financial Administration, but other state authorities may feel more bound by EU regulations and require a qualified certificate.
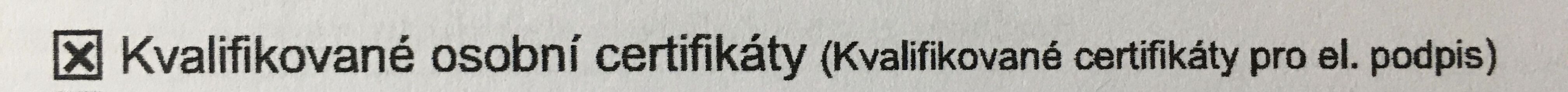
Every issued certificate must be made public, otherwise it is not trusted. However, since it must in principle contain your personal data, the CA needs your consent to do so. However, it is interesting if you do not give her that consent. What will happen next, no one knows. The state administration must also accept a signature that was created by a certificate that is not publicly available.
Although it is possible to conclude Smlouvu o poskytování certifikačních služeb for an indefinite period of time, I would avoid it. If every certificate expires once, why shouldn't the contracts?
Unlike I.CA or eIdentity, PostSignum cannot generate and send a request via a web browser. PostSignum advertises a proprietary application as the easiest option. Be warned in advance that the first thing you will have to do after launching this application is to find out where it has been automatically installed, change its behavior so that the DPI controls the OS, and then run it again to be able to read something in it. Make a note of this location somewhere, because once you use it, you won't simply uninstall it from your system. It does not have the classic Microsoft Windows Installer, but something proprietary that copies some files somewhere, which are then launched.
I do not understand the impossibility of submitting an application via a web browser, because it is a multiplatform option in principle and the CA does not have to program utility applications for all conceivable operating systems (Windows, macOS, Linux) in combination with all possible instruction sets (x86, x86-64, ARM, ARM64). You have a total of 12 combinations on which you have to keep an eye on the functionality of the cryptographic libraries. Parade. Will we see support for Power ISA or RISC-V architectures in the future? I don't know. But I suspect that Chromium will be ported to them much sooner.
Apparently, an even “better” option is to generate the request yourself and bring it to the post office on a storage device with a USB bus (from the type of memory used popularly known as a flash drive). If you do, throw away the used flash drive right away. After returning from the mail, it is also not safe to connect it to the operating system for formatting. Unless you own special hardware that can do nothing but format flash drives. If you think I'm exaggerating, read what Stuxnet was.
The Czech Post’s computer network cannot be considered secure simply because it is possible to connect a flash drive to a computer in its network from anywhere from the outside. The situation may be more serious than some people admit.
Installing the certificate
Certificate with QSCD save flag
To import a certificate from QCA (the public part of the certificate without a private key), eObčanka – správce karty can be used. First, you have to switch it to the extended view and then you can import the issued certificate to the already generated private key.
If you generated the application using the iSignum application, just click on the Stažení certifikátu button after receiving the certificate, then on *Check issued certificates * and install the newly found certificate on the eOP this way. It’s actually very easy and if you are just renewing the certificate, it will only take a minute to generate a new certificate this way. However, you must have a valid contract with the Czech Post for the provision of certification services.
Certificate for a private key stored in Windows
If you just need to have the certificate stored in Windows, all you have to do is install it. However, it is better to have a certificate on the eOP, as this will guarantee that it will be protected by another password and will only be accessible to the operating system as long as the eOP is physically in the reader.
Moving the private key from Windows to eOP is very easy. The iSignum app will do it for you. All you have to do is export the private key from Windows to a file (PKCS#12 format, PFX file extension) and then import it into eOP.
Alternatively, you can use mmc.exe to export, add the Certifikáty snap-in for the user account, find your certificate and export it with the private key. You can use the eObčanka – Správce karty application to import.
After successful import, do not forget to delete the certificate from Windows. I mean both removing a certificate from the certificate store in Windows and deleting the file with the private key (of course, not just moving it to the trash).
The point of everything is to have the private key on the device, from where it can no longer be exported. However, you have to register it in the application to the operating system. This is so that the operating system has an overview of what certificates are hypothetically available. This is done in application eObčanka – Správce karty.
When you do this, it’s a bit confusing that Windows then looks like the private key is stored on your PC’s hard drive (which is a scary idea). But in reality, it is not. However, if an application requests it, the request is redirected to the appropriate hardware (i.e., a qualified resource). However, because this resource is usually connected via USB, the application can access it directly and bypass the Windows certificate store. Both methods are possible. In practice, therefore, registering a certificate in Windows is only necessary so that applications that can only read certificates from the Windows certificate store can use the electronic signature. Such an application is, for example, Microsoft Outlook.
Use in the Tax Portal applications of the Financial Administration
If you wanted to sign electronically with the financial administration, you had to have Internet Explorer and the ActiveX add-on until 1 September 2020. You have signed by opening the file with your private key directly in the browser. However, support for this browser will end on 09/03/2021. Probably for this reason, the Financial Administration has issued the application of ePodpisFS. At first glance, it might be a matter of wonder why only now, but compared to South Korea, we are not so bad. It also got rid of their digital ID dependence on the ActiveX-based add-on only this year. However, given that ActiveX is from 1996, it is at least remarkable.
The already mentioned ePodpisFS application is written in Java. After it is launched, its test is immediately available. Clicking on the Spustit test button will search for those personal certificates in your operating system that are qualified and have not expired or revoked. During the test, it is even checked whether the current version of the application is still up-to-date.
The application has a normal installer, so it can be uninstalled normally. The Windows version is only 32-bit so far, although the paragraph with supported operating systems says otherwise. I wonder when we will see the ARM64 version. Apple introduced its M1 processor the day before yesterday and Microsoft its SQ1 more than a year ago. So when choosing your computer, keep in mind that sometimes you may also want to pay taxes.
You can also log in to the Tax Portal using this application and a qualified certificate. However, the problem is that the portal does not know your ID card of the Ministry of Labour and Social Affairs. It is a pity that the portal does not keep track of the lists of qualified certificates issued. He would know from them which ID card of the Ministry of Labour and Social Affairs should pair with his user accounts. First, you need to log in to the Tax Portal by clicking on Přihlásit NIA. Which means through the Portal of the National Point for Identification and Authentication.
Logging in and signing are two completely different operations. But if you already have a smart card reader and an ID card with a contact chip, you can log in via NIA with it. A certificate is not needed for this. It is only needed to sign.
There are several ways to submit and sign a document. One of them is:

The app will then guide you. First, you select the storage type (operating system or qualified resource) and then the specific certificate. The next steps depend on the specific hardware, but entering the PIN directly into the reader works as expected.
If the PIN (and this time it really means the PIN, not the IOK) is entered correctly, the reader will issue the ePodpisFS application with the private key to the certificate. He then signs and sends the document with it.
Summary
Why can't the state issue an identity card (ID card) with an already installed qualified certificate with the ID card of the Ministry of Labour and Social Affairs with the attribute of storage on a secure device (with the export of the private key prohibited), which would have an expiration date identical to the end of the card’s validity? After all, the vast majority of cryptographic smart cards can generate a private key in the chip itself. Physically, this can happen at the moment when you pick up the ID card.
Backing up the private key, i.e. not even exporting it, might not be necessary. If you lost your license, it wouldn't matter. Instead of restoring the certificate from a backup, you would simply have a new certificate. And as a bonus, the authority could automatically invalidate the certificate stored on it immediately when reporting the loss of the ID card.
Having apps on the Microsoft Store is a double-edged sword from a security point of view. While apps would update automatically, Microsoft would have to commit not to remove them from the store without government approval. Because if that happened, all electronic registries would stop working. It would be similar with Apple and its Mac App Store. On the other hand, the Linux versions of these applications would work all the time, so people would install Linux if necessary and move on. That’s why I think Linux support is important. Without government applications for Linux, it is not possible for them to appear in the application stores tied to a commercial proprietary operating system.
Finally
Electronic signatures are nowhere near what they should be. The most difficult thing about the whole thing is to get a qualified certificate and secure handling of its private key. If you received it directly with your ID card, where they verify your identity anyway, everything would be much easier. The applications of eObčanka and ePodpisFS seem to me to be sufficiently advanced, and if the development continues at the current pace, perhaps one day the state, in cooperation with the EU, will simplify the payment of taxes more than make it more unpleasant. However, the current login with a personal certificate is from the Stone Age, perhaps even beyond the law. The certificate does not state that it can be used in this way. How does the Financial Administration want taxpayers not to circumvent the law when it does it itself? In addition, from the point of view of what is common on the Internet, it is completely untrustworthy. This is because it is common to log in with a personal certificate already at the stage of establishing a connection to the server using TLS (transport layer security). The standard for client certificates dates back to 2008. It works everywhere. But why make things simple when it can be complicated?
